Windows Event Logs - Applications and Services
LogicMonitor does a great job capturing Application, System and Security events from the Windows Event Log via WMI. We are trying to expand our Event Log monitoring to include events from the Applications and Services Logs. These cannot be collected by LogicMonitor via WMI but the documentation says we should be able to collect these using Event Log subscriptions and write them to the Application log. We have an event log subscription set up on one Windows server collecting events from others. They are source initiated subscriptions, specifically AppLocker error events which we have being collected and written to the Application log of the collecting server. The events are making it to Application Log but we are not receiving alerts in LogicMonitor. I have tried a custom Event Source and even used the built-in one which should be collecting all Application Event Log errors occurring on the server. We get alerts for application errors that occur on the server - just not the AppLocker errors despite them being listed in the log.
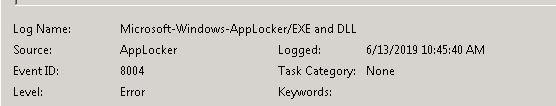
I noticed the Log Name in these collected events shows "Microsoft-Windows-AppLocker/EXE and DLL" event though they are in the Application log. Could this be the reason LogicMonitor is not alerting on them? They are not found when using the Event Source Testing tool either.
Wondering if anyone has any tips on how to use a subscription to alert on events from the Applications and Services Logs.