Advisor
AdvisorWhat permissions needed for ssh user on Linux boxes to monitor
So as a test we created a new user on a linux box and specified this user on the properties of the linux system (ssh.user/ssh.pass) Forced a Active Discovery and DS re-match and its been 1hr so far and its still under "minimal monitoring".
We don't want to use snmp, so for ssh only systems what are the required permissions needed for ssh to work? Does the user have to be part of the root group?
Was looking at this page: https://www.logicmonitor.com/support/monitoring/os-virtualization/linux-via-ssh-monitoring but there is no mention of permissions needed on the user.
So what then do I need to do to get LM to use the Linux_SSH DS to monitor this box? The system.categories property is empty.

Okay: figured it out. ?
So first for the Linux_SSH DS's to be applied they only work on devices who's system.categories contain hasCategory("Linux_SSH"). So I checked the property source "addCategory_Linux_SSH" and when I tested it against the device above it failed. ?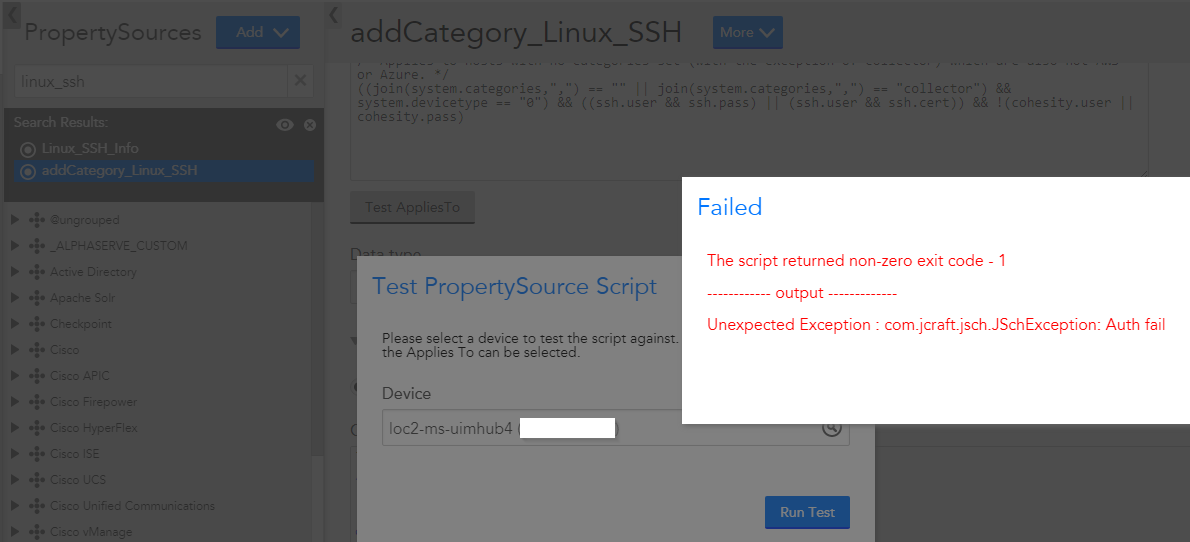
I re-entered the password, retested and then the test above worked. The system.categories got populated with "Linux_SSH" and then forced a AD and DS rematch and I finally got the Linux_SSH DS's to work:
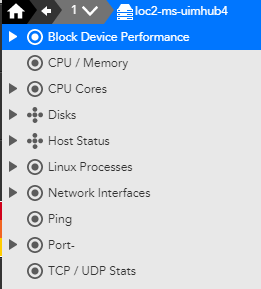
Ok so a 'regular' Linux use can be used and works. I forgot the whole process flow of how things are detected, categorized, then DS's applied. I'll add this to my check list of things to check next time adding something and it doesn't work.
Thanks Folks!!!