Hey @joshlowit1,
This one is a little trickier than it appears at first glance - firewall profile status/ activity isn't available through WMI, which leaves us with the command line - and PowerShell - meaning we need to do some scripting. There are a couple of relevant commands that return some information from Windows:
I whipped up a quick PowerShell-based batchscript DataSource you can start with - it uses Get-NetFirewallProfile to determine if the firewall profiles are enabled - but unfortunately not if they are "connected." This ought to cover your use case though - if you have the profiles disabled for Domain, Public, and Private, and one becomes enabled (regardless of connection status,) this module should alert. (See the bottom of the post for a graphic that helps explain this confusing terminology.)
Windows_Firewall_ProfileStatus has locator code CP6KLA and should be available for import as soon as I run it past our monitoring team.
Let me know if you have any thoughts - it's a good bet that someone out there can integrate the "connected" profile piece with the enabled ones - with a little more work on the scripting side...
Cheers,
Kerry
NB: Here's the "collection" half of the DataSource for those interested - because we can monitor Windows both through integrated (and not) authentication, you'll notice that we use one of two different PowerShell remoting methods based on the presence of manually-defined credential properties:
#LogicMonitor PowerShell Script Template 5.0
#If present, ingest hostname and credentials from LogicMonitor device properties.
$hostname = '##SYSTEM.SYSNAME##';
$wmi_user = '##WMI.USER##';
$wmi_pass = '##WMI.PASS##';
#Are WMI credentials set? (Are the device properties unused or empty?)
if ( (($wmi_user -like '*WMI.USER*') -and ($wmi_pass -like '*WMI.PASS*')) -or (($wmi_user -eq '') -and ($wmi_pass -eq '')) )
{
$use_credentials = $FALSE;
$method = "Invoke-Command";
}
else
{
#Convert username + password into a credential object for non-integrated domain authentication
$use_credentials = $TRUE;
$method = "Import-PSSession";
$remote_pass = ConvertTo-SecureString -String $wmi_pass -AsPlainText -Force;
$remote_credential = New-Object -typename System.Management.Automation.PSCredential -argumentlist $wmi_user, $remote_pass;
}
#If we found credentials above, we will use them.
if ( $use_credentials ) {
#Establish a persistent remote PowerShell session from the collector to the device
$session = New-PSSession -ComputerName $hostname -Authentication kerberos -Credential $remote_credential;
#Import the remote PowerShell session and limit the amount of commands to import for efficiency
Import-PSSession $session -CommandName Get-ADDomainController -AllowClobber | Out-Null;
#Execute proxied remote commands on the local collector
$profiles = Get-NetFirewallProfile -PolicyStore ActiveStore
forEach($profile in $profiles) {
$name = $profile.Name
$enabled = $profile.Enabled
switch($enabled)
{
"True" {$enabled = "1"}
"False" {$enabled = "0"}
}
Write-Host $name".Enabled="$enabled
}
Remove-PSSession $session
Exit
}
#If we did NOT find credentials above
else {
#Attempt integrated authentication using collector service account in the absence of credentials.
Invoke-Command -ComputerName $hostname -ScriptBlock {
#Execute remote commands remotely and capture the output
$profiles = Get-NetFirewallProfile -PolicyStore ActiveStore
forEach($profile in $profiles) {
$name = $profile.Name
$enabled = $profile.Enabled
switch($enabled)
{
"True" {$enabled = "1"}
"False" {$enabled = "0"}
}
Write-Host $name".Enabled="$enabled
}
}
Exit
}
Exit
Windows Firewall example: (Domain Profile = Disabled, Connected. Private = Enabled, Not Connected. Public = Enabled, Not Connected.
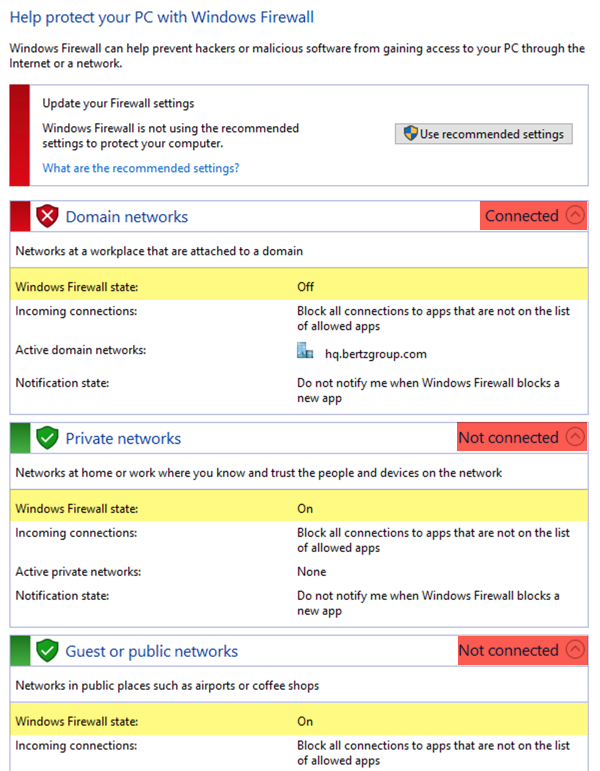
The above datasource will alert on the instances for the Private and Public firewall profiles, as they are both enabled, regardless of connection status.
 Neophyte
Neophyte Neophyte
Neophyte
