Forum Discussion
- Stefan_W
Neophyte
That was from a pop-up that appeared in the portal yesterday.
- Anonymous
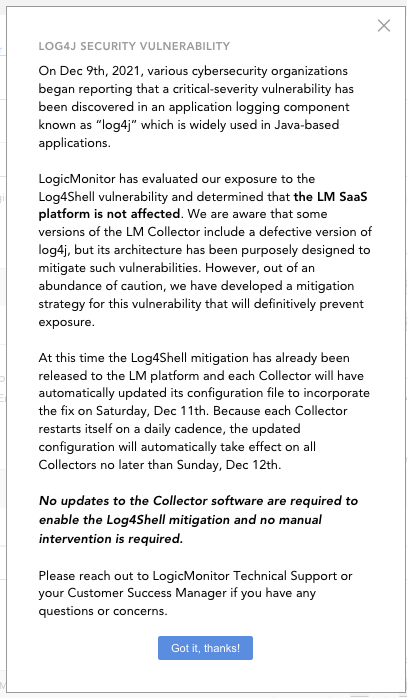
Yes, the above pop up should have appeared the first time an administrator logged in after Saturday:
QuoteOn Dec 9th, 2021, various cybersecurity organizations began reporting that a critical-severity vulnerability has been discovered in an application logging component known as “log4j” which is widely used in Java-based applications.
LogicMonitor has evaluated our exposure to the Log4Shell vulnerability and determined that the LM SaaS platform is not affected. We are aware that some versions of the LM Collector include a defective version of log4j, but its architecture has been purposely designed to mitigate such vulnerabilities. However, out of an abundance of caution, we have developed a mitigation strategy for this vulnerability that will definitively prevent exposure.
At this time the Log4Shell mitigation has already been released to the LM platform and each Collector will have automatically updated its configuration file to incorporate the fix on Saturday, Dec 11th. Because each Collector restarts itself on a daily cadence, the updated configuration will automatically take effect on all Collectors no later than Sunday, Dec 12th.
No updates to the Collector software are required to enable the Log4Shell mitigation and no manual intervention is required.
Please reach out to LogicMonitor Technical Support or your Customer Success Manager if you have any questions or concerns.
- DanB
Advisor
Is there something that LM will release more official that we can share with our clients. I've been asked many times today if we can delete these files or uninstall LM Collectors b/c these boxes are still turning up as still 'venerable' by this vulnerability scans.
- Anonymous
Haha, 'venerable' is a good thing. "Vulnerable" is not.
Official notice should be coming out some time this week.
- 2 hours ago, Steve the IT Guy said:
To confirm the configuration update, look in C:\Program Files (x86)\LogicMonitor\Agent\Conf\watchdog.conf for "-Dlog4j2.formatMsgNoLookups=true"
Thanks!
- Anonymous
I believe this is the highest priority activity for us right now. It should drop soon; i believe the decision has been to remove it entirely since it's not being used anyway. I understood log4j to be included in the Collector but not actually used in any capacity. Most vulnerability scanners can detect whether or not log4j is present, but not if the vulnerability can actually be exploited. So while the current version of the Collector may show up as containing log4j, that doesn't necessarily mean that the vulnerability exists and can be exploited. To be clear, a new collector version will be the third method of protecting against any log4j exploitation on the Collectors. The second is the configuration change that was already pushed out; the first is the fact that log4j isn't actively used by any of the Collector components.
There are end customers of ours disabling Collectors due to this issue. Any chance that a patch will become available with the updated log4j libraries in it?
Or the removal of the log4j libraries (as you mention in another post)?
- Mike_Rodrigues
Product Manager
We're working on a patched version of the collector with updated log4j, it's scheduled to drop soon.
Official communication is here and will be updated as we know more. Thanks @Michael
Related Content
- 2 years agoAnonymous