Forum Discussion
29 Replies
- Mosh
Professor
Thanks @Michael Rodrigues.
We would much prefer that LogicMonitor updates the log4J libs in the collectors to 2.16 minimum as there are also vulnerabilities in 2.15.
- 4 hours ago, Mosh said:
@Michael Rodrigues@Stuart Weenig
For info, Log4J 2.16 also have a exploitable vulnerability:
https://nvd.nist.gov/vuln/detail/CVE-2021-45105
https://logging.apache.org/log4j/2.x/security.htmlWe are upgrading all of our own enterprise products to use 2.17. Will LogicMonitor be upgrading to 2.17?
2nd this. Though the vulnerability is less severe, does LogicMonitor plan to update to 2.17 given the high visibility of these vulnerabilities? If so, when can we expect an updated collector?
Thank you
- Mike_Moniz
Professor
Looks like LM just released 31.002 with Log4J 2.17, https://www.logicmonitor.com/support/gd-collector-31002
Has anyone been able to confirm log4j has updated to 2.17? Linux collectors on 31.002 are still showing 2.13 jars.
- Just now, Mosh said:
Hi @alan, where are you seeing JARs for 2.13?
/usr/local/logicmonitor/agent/lib/log4j-1.2-api-2.13.2.jar
/usr/local/logicmonitor/agent/lib/log4j-api-2.13.2.jar
/usr/local/logicmonitor/agent/lib/log4j-core-2.13.2.jar - Mosh
Professor
11 minutes ago, alan said:/usr/local/logicmonitor/agent/lib/log4j-1.2-api-2.13.2.jar
/usr/local/logicmonitor/agent/lib/log4j-api-2.13.2.jar
/usr/local/logicmonitor/agent/lib/log4j-core-2.13.2.jarMine are all 2.17 (all mine are Windows):
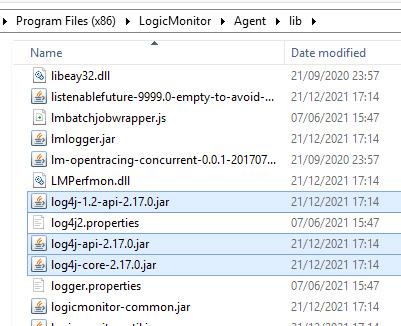
- 1 hour ago, alan said:
Has anyone been able to confirm log4j has updated to 2.17? Linux collectors on 31.002 are still showing 2.13 jars.
My mistake, was using the locate command and didn't realize the locate DB does not automatically update. log4j is at 2.17 after the linux collector update.
Folks - We're going to need YAP (Yet-Another-Patch) to get log4j 2.17.1 packages out to Collectors.
Straight from the horses' err... mouth....
https://logging.apache.org/log4j/2.x/QuoteApache Log4j 2
Apache Log4j 2 is an upgrade to Log4j that provides significant improvements over its predecessor, Log4j 1.x, and provides many of the improvements available in Logback while fixing some inherent problems in Logback’s architecture.
Important: Security Vulnerability CVE-2021-44832
Summary: Apache Log4j2 vulnerable to RCE via JDBC Appender when attacker controls configuration.
Details
Apache Log4j2 versions 2.0-beta7 through 2.17.0 (excluding security fix releases 2.3.2 and 2.12.4) are vulnerable to a remote code execution (RCE) attack where an attacker with permission to modify the logging configuration file can construct a malicious configuration using a JDBC Appender with a data source referencing a JNDI URI which can execute remote code. This issue is fixed by limiting JNDI data source names to the java protocol in Log4j2 versions 2.17.1, 2.12.4, and 2.3.2.
Mitigation
Upgrade to Log4j 2.3.2 (for Java 6), 2.12.4 (for Java 7), or 2.17.1 (for Java 8 and later)
Reference
Please refer to the Security page for details and mitigation measures for older versions of Log4j.
FYI