Forum Discussion
11 Replies
- aarkkelin
Neophyte
Just wanted to toss a note in here saying I stumbled upon this by accident but was actually something we were actively looking into how to monitor this on CheckPoints. So, thanks for opening the original thread,
@Nishil Vachhani . Secondly, I was able to build a datasource to monitor a specific tunnel. It’s a bit tedious if you have to repeat that for multiple tunnels at a site. But for anyone looking to just monitor a few, it’s definitely doable using the OID info in the CheckPoint article linked in the comments above. It’s not the cleanest thing ever and it’s definitely something I hope LM builds into their standard CheckPoint datasources and tidies up a bit. But for now, this seems to get the job done.- dlebouef
Neophyte
How did you set your DataPoint(s)?
I am trying to monitor some tunnels on a CP and this is what I get when trying to poll the DS:
Fail to get the result of this oid OID is 1.3.6.1.4.1.2620.500.9002.1.3.X.X.X.X.0 Raw value is Tunnel1 : 3 , Tunnel2 : 3 , Tunnel3 : 3 , Tunnel4 : 3 , Tunnel5 : 3 , Tunnel6 : 3 , Tunnel7 : 3 , Tunnel8 : 3 , Tunnel9 : 3 , Tunnel10 : 3 , Tunnel11 : 3 , Tunnel12 : 3 , Tunnel13 : 3 , Tunnel14 : 3 , Tunnel15 : 3 , Tunnel16 : 3 , Tunnel17 : 3 , Tunnel18 : 3 , Tunnel19 : 3 , Tunnel20 : 3
It's getting the raw values correct but not sure how to configure the DataPoint for these. Do I need to create a DataPoint for each tunnel?
Thanks!
- Anonymous
No, you need to create instances through SNMP discovery. It looks like this would simply be "value" discovery through SNMP, and you should be able to use almost the same OID: 1.3.6.1.4.1.2620.500.9002.1.2. The result of that walk should give you IDs (the ip addresses) and names (Tunnel1-Tunnel20). By picking "value" discovery, it'll use the IDs as the wildvalues and the names as the wildaliases, matching the definition in the MIB.
Once you have that, your datapoint would simply use a key of 1.3.6.1.4.1.2620.500.9002.1.9.##WILDVALUE##. You can bring in the other numeric datapoints by swapping out the 9 for 3 (state), 8 (priority), 9 (probstate), 10 (peer type), or 11 (tunnel type).
- Anonymous
Ug, the sign in process to get to the academy. So broken, especially if you have SSO configured. Please tell me the advances made with the multi-SSO platform will provide a single login page with Skilljar redirection built in.
- Eric_H
LM Champion
There’s also a quick 7min video tutorial on making an SNMP DataSource in our LearningBytes training series here…
Learning Byte: Making an SNMP DataSource
https://academy.logicmonitor.com/making-an-snmp-datasource/1329215 - tswisdom
LM Conqueror
Much obliged Nishil,
Evaluating our core Checkpoint modules, it doesn’t appear we’re currently capturing IPSec Tunnel data, nor do we have a generic IPSec Tunnel module. I also evaluated community modules in the exchange, and didn’t surface anything that’d collect this data. With that said, given you already have the appropriate OID’s, you should certainly be able to capture the data via custom datasource, we touch on how to do so here. You may also wish to take a moment to submit feedback through your portal requesting IPSec Tunnel Monitoring be added for Checkpoint devices.
Warm regards,
Tyler Wisdom - Anonymous
If you have the OIDs, have you attempted to build the DS yourself?
@Stuart Weenig - I was reading the Checkpoint article it mention about to monitor state of the VPN tunnel via SNMP OID 1.3.6.1.4.1.2620.500.9002.1.3 and SNMP OID 1.3.6.1.4.1.2620.500.9003.1.3. I don’t think those OID is added in the Checkpoint core.Here the link for the article.
@tswisdom - The device type is the Firewall and Vendor is the Checkpoint.- tswisdom
LM Conqueror
Hello Nishil, can you confirm the device type and vendor in which the IPSec tunnels are configured?
- Anonymous
I don’t know what custom OID you might be referring to, but we do have some significant customizations to that DS.
- We have modified the script to add another output to detect if the device is a standby device.
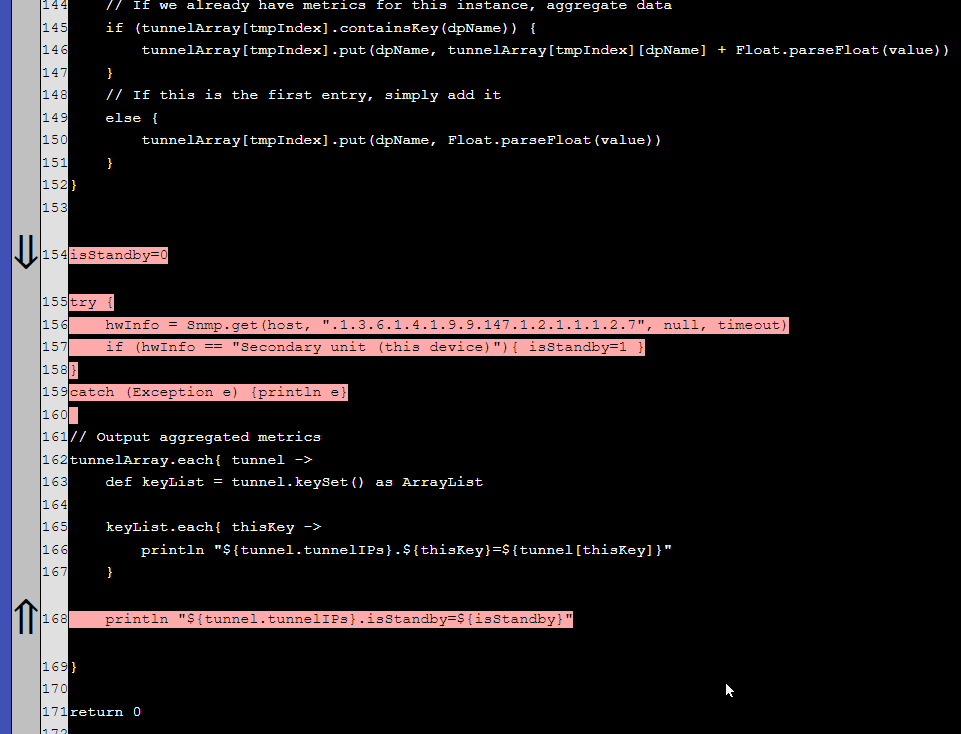
- We created a datapoint to store that:
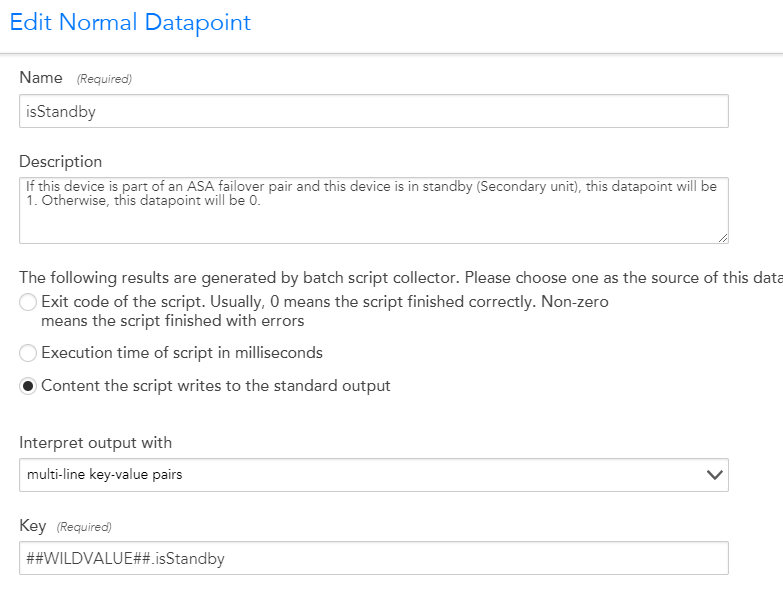
- Then we modified the TunnelActiveTime_Seconds datapoint:
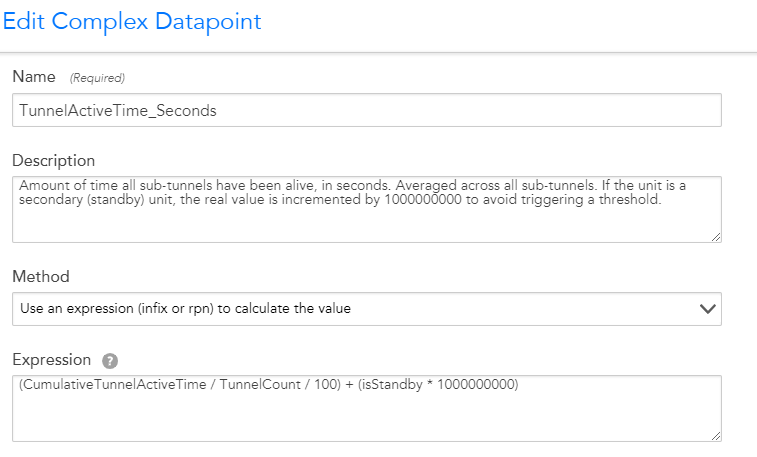
This might not be what you are looking for, but it helped us reduce alerts for when a secondary unit was offline.
- We have modified the script to add another output to detect if the device is a standby device.