 Neophyte
NeophytehostProps.set() workaround
Hey all,
So it looks like I'm not the only one trying to find a way to update device properties on the fly using the collector. 
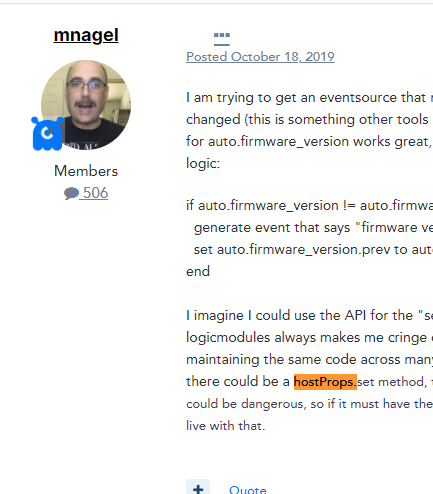
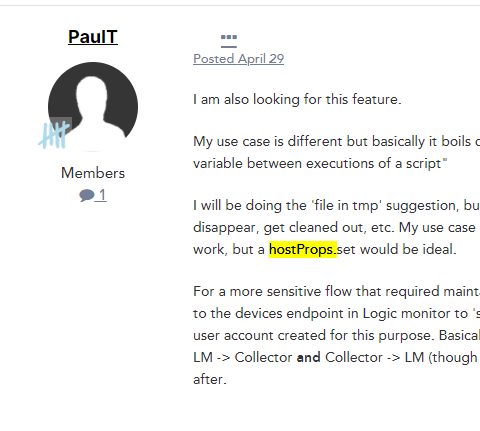
I'm not sure why a hostProps.set() isn't a working function yet but my workaround involved making API calls when device properties needed to be updated right away. Of course, it doesn't make sense to have a collector server do the extra work of making API calls in order to accomplish this - especially considering it could cause downstream effects like API throttling. So I went through the effort of learning some java and dissecting the collector jar files to figure out if there was some other way to do it. Here's what I found:
import com.santaba.agent.debugger.*
println "Updating property: system.${LMObj} :: OldValue: ${hostProps.get("system.${LMObj}")} :: NewValue: ${currentObj}"
task = "!hostproperty action=add host=${hostProps.get("system.hostName")} property=${LMObj} value=${currentObj}"
HostPropertyTask updater = new HostPropertyTask(task)
updater.run()
println updater.output
return updater.exitCode
A few words of caution:
- ❗❗❗❗❗ This code updates SYSTEM properties, NOT AUTO.* properties. This is a very important distinction. This functionality could really ruin your day if you go deploying a datasource that updates properties such as system.ips, system.hostname, system.<user>, system.<password>, etc. ❗❗❗
- This does not work unless you update your Agent config file (agent.conf) on the collector (and restart the service for it to take effect):
❌ groovy.script.runner=sse
✔️groovy.script.runner=agent
- LogicMonitor could break this functionality at any time in a future release. I've only tested this on the latest few general releases and it appears to work well - but it could break at any time.
- The audit log won't tell you that the host properties were modified. Instead, you only see the results of the change: auto groupmembership, autodiscovery, SDT, etc. If the change itself gets logged somewhere, I don't know where you might find it.
Lastly, you definitely should not be using this method each every time your datasource runs. Make sure to implement some logic to only update the property if and when needed. I have no idea how well this code snippet scales outside of a few hundred resources per minute and since I haven't found any documentation on it, I'm using it sparingly and not yet heavily relying on it to work 100% of the time. That being said, so far it seems to work quite well. Feel free to report how well it worked out if you aren't afraid to scale it like crazy and measure the performance.
