 Advisor
AdvisorHow to get the Certificate Common Name (FQDN) in the alerts description
Hello,
I am using the two script from Cole McDonald:
I've lightened the load slightly on the winCertCheck (which is technically no longer the same DS as I've replaced the entirety of the scripts with simplified .NET based powershell scripts to avoid using invoke-command which tends to lead to some resource constraint issues. This should help though, will keep the same instances alive from the old code as the output is identical to the previous version by @Jonathan Arnold:
##--------------- Discovery ------------------##
$readOnly = [System.Security.Cryptography.X509Certificates.OpenFlags]"ReadOnly"
$localMachine = [System.Security.Cryptography.X509Certificates.StoreLocation]"LocalMachine"
$store = new-object System.Security.Cryptography.X509Certificates.X509Store( "\\##SYSTEM.SYSNAME##\root", $localMachine )
$store.Open( $readOnly )
$store.Certificates `
| Select-Object {$_.Thumbprint + "##" + $_.Thumbprint + "##" + $_.Subject + $_.CommonName} `
| Format-Table -HideTableHeaders
##--------------------------------------------##
##-------------- Counters --------------------##
$readOnly = [System.Security.Cryptography.X509Certificates.OpenFlags]"ReadOnly"
$localMachine = [System.Security.Cryptography.X509Certificates.StoreLocation]"LocalMachine"
$store = new-object System.Security.Cryptography.X509Certificates.X509Store( "\\##SYSTEM.SYSNAME##\root", $localMachine )
$store.Open( $readOnly )
$store.Certificates `
| Where-Object {($_.Thumbprint -like "##WILDVALUE##")} `
| Select-Object @{
Name = "DaysUntilExpire"
Expression = {((Get-Date -Date $_.NotAfter) - (Get-Date)).Days}
} `
| Format-List
##--------------------------------------------##
(please note the line continuations to help readability of the code)
As always, neither I nor Beyond Impact warranty this code. It's working in our environment, I can't guarantee it'll work in yours. This doesn't account for anything that needs credentials other than what the collector uses.
==========================================================================================================================
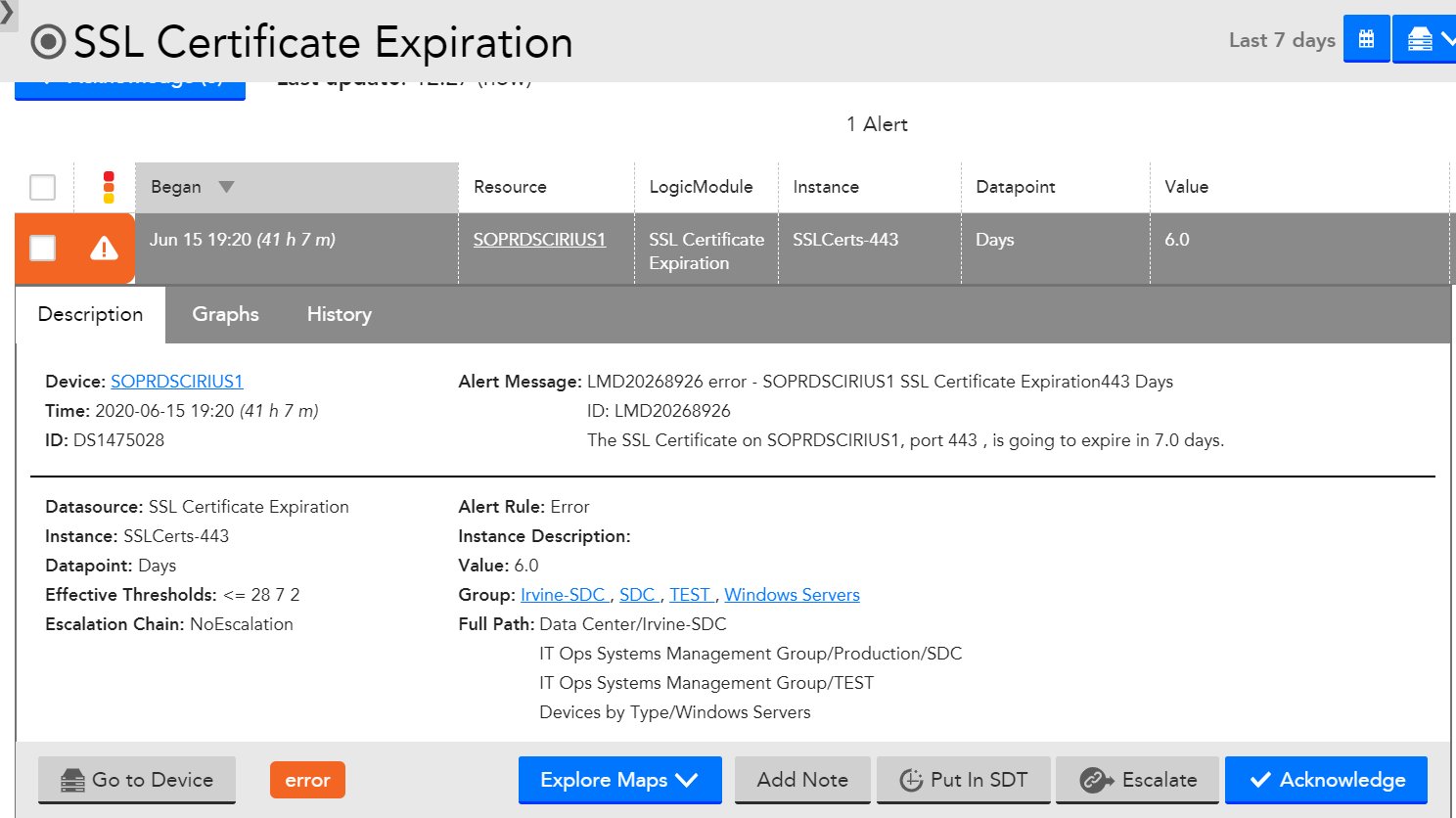
But when testing them on a current alert
I could not get the correct common name displayed... and I do not see the certificate listed in the alert in the list of certificates produced by the script...
I might have missed something!!!
Thanks,
Dom
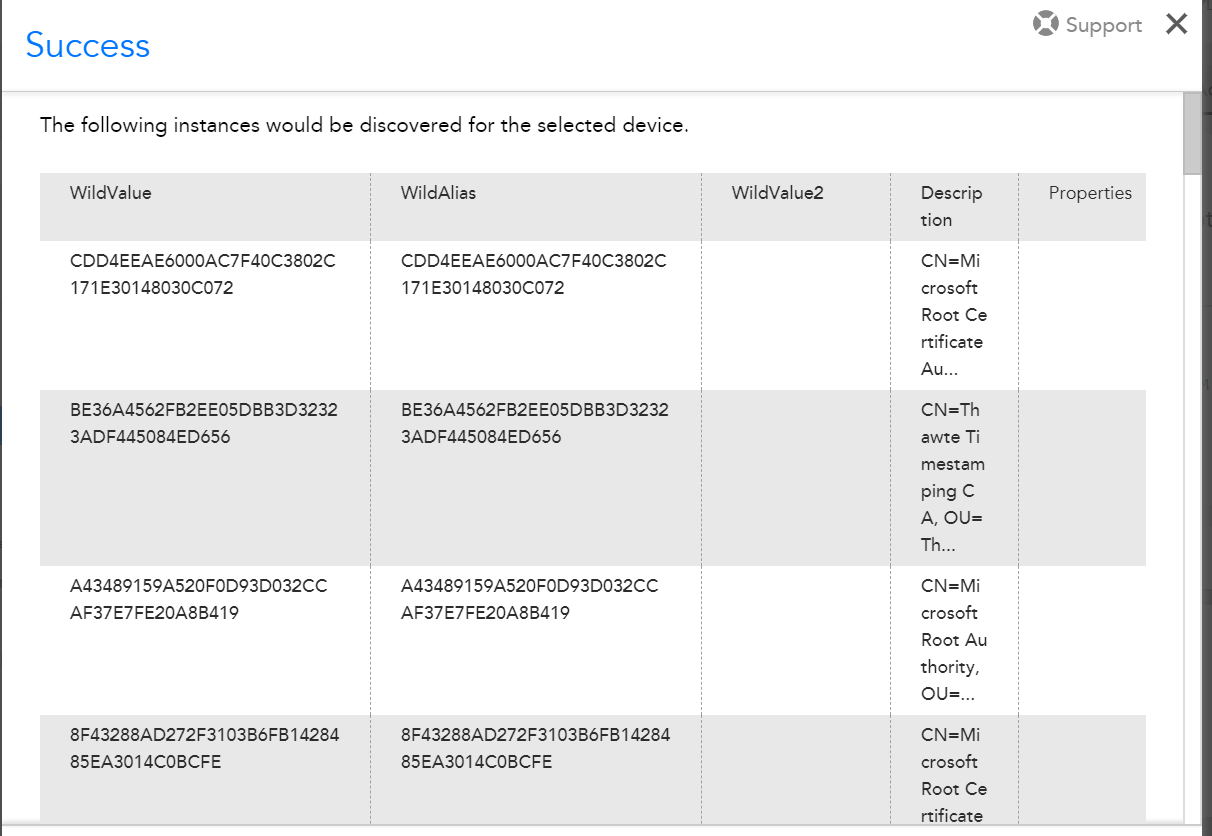
Thanks for your patience Stuart...
I found the location
##$store = new-object System.Security.Cryptography.X509Certificates.X509Store( "\\##SYSTEM.SYSNAME##\root", $localMachine )##
$store = new-object System.Security.Cryptography.X509Certificates.X509Store( "\\##SYSTEM.SYSNAME##\my", $localMachine )Now I have the good certificate listed... I need to add as you said the expiration date set to combined both...
Thanks,
Dom
