 Employee
EmployeeLDAP Binding Security - Active Directory Domain Controllers
In December of 2019, Microsoft published a release announcing upcoming changes to LDAP channel binding and LDAP signing requirements for domain controllers.
QuoteThere is a vulnerability in the default configuration for Lightweight Directory Access Protocol (LDAP) channel binding and LDAP signing that may expose Active directory domain controllers to elevation of privilege vulnerabilities. Microsoft Security Advisory ADV190023 address the issue by recommending the administrators enable LDAP channel binding and LDAP signing on Active Directory Domain Controllers. This hardening must be done manually until the release of the security update that will enable these settings by default.
Microsoft intends to release a security update on Windows Update to enable LDAP channel binding and LDAP signing hardening changes and anticipate this update will be available in March 2020.
This is a good thing (!) , as one Microsoft blogger puts it:
QuoteIf I told you that there was a 90% plus chance that your Domain Controllers allowed receiving credentials in clear text over your network, you would probably wouldn't believe me. If I went a step further and told you that nearly half of the customers I visit for AD security assessments not only allowed them, but had extremely privileged accounts such as Domain Admins credentials traversing the network in clear text, you would probably think "that wouldn't happen on my network", well that's what they all told me too
However ... security requires preparation, and this particular change means Windows administrators will want to configure servers before the patch is applied. If you're managing dozens or hundreds of servers, identifying which resources need attention could be a time consuming proposition. Luckily (per the post above) we have a couple methods to look for vulnerable domain controllers.
So, with that in mind, the LogicMonitor DataSource Win_LDAP_Binding_Security uses PowerShell (specifically, Get-WinEvent) to comb through the (first 10,000 events of) Directory Services log for the presence of events with Event IDs 2886 and 2887 (and generates an alert if it finds anything.) Which again, means:
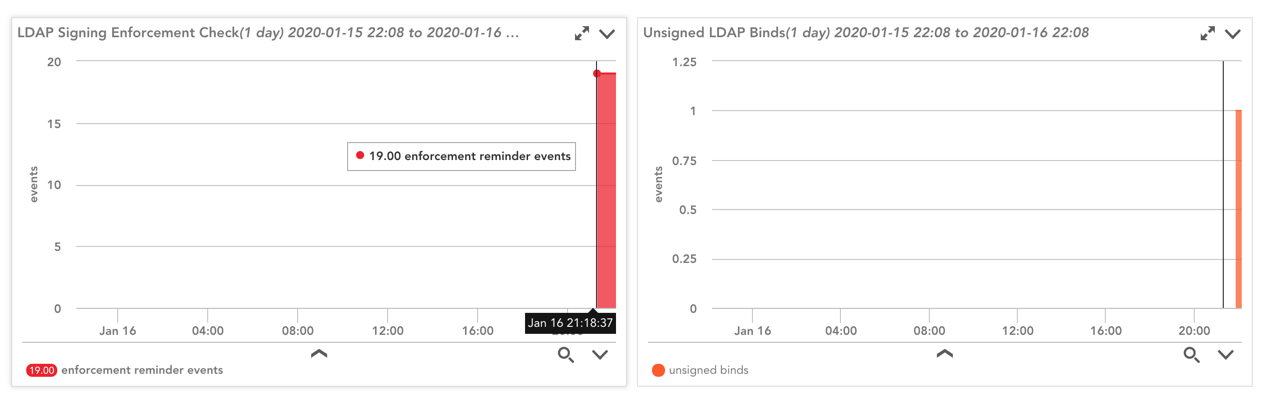
QuoteIf any of your Domain Controllers have the 2886 event present, it indicates that LDAP signing is not being enforced by your DC and it is possible to perform a simple (clear text) LDAP bind over a non-encrypted connection.
Our next port of call is the 2887 event. This event occurs every 24 hours and will report how many unsigned and clear text binds have occurred to this DC. If you have any numbers greater than zero, you have some homework to do.
Hopefully this saves somebody some time - and helps bring visibility to a potentially important security vulnerability in the network!
Win_LDAP_Binding_Security should be available shortly via locator code FJDAJZ